The 1390 Standard
Another 10-billion unit market:
Universal house meters/resources become intelligent
if linked to a centralized DB accessible from Internet
Success story of ET Technologies!
Who comes first to China?
Off-hook versus on-hook
Major issue-low VLSI area solution
for high production volume
SUBOPTIMAL DETECTION
FOR SIGNAL TYPES
DEFINED BY THE IEEE 1390 STANDARD
Miljan Vuletic,
Goran Davidovic, Veljko Milutinovic
Department of Computer Engineering
School of Electrical Engineering
University of Belgrade
POB 35-54, 11120 Belgrade, Serbia, Yugoslavia
miljan@galeb.etf.rs
davidovic@buef31.etf.rs
vm@etf.rs
å
Introduction
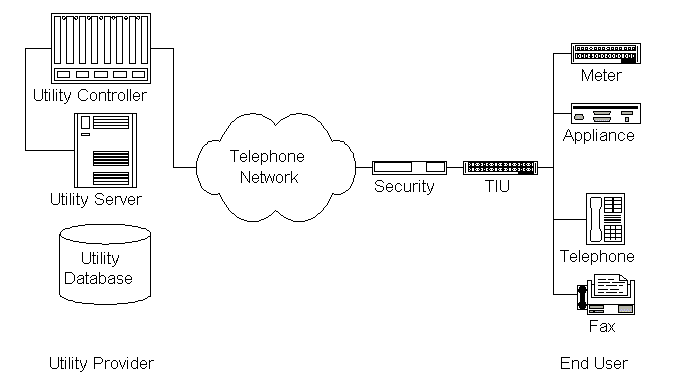
UTSA (Utility Telemetry Service Architecture):
- Optimal detection methods
- Suboptimal detection methods (DMF, SAS, WPD, BMF)
- TIU: Telemetry Interface Unit
2. Problem Definition
SAT (Single Alert Tone) and DAT (Dual Alert Tone) detection
SAT: {f1, f2, f3, f4, f5, f6, f7, f8, f9}
DAT:{fg & fx, where fx is one of f1, f2, f3, f4, f5, f6, f7, or f8}
Frequency values:
f1=375.2Hz, f2=404.3Hz, f3=468.0Hz, f4=495.8Hz, f5=520.6Hz, f6=548.0Hz, f7=562.8Hz, f8=578.4Hz, f9=1633.0Hz, fg =1827.0Hz
3. Existing Solutions
Newely adopted standard IEEE 1390
Application of optimal detection methods (DSP)
R2 signal detector developed by ² TELLCO² (TUA 0096AA)
4. Suggested Solution
Using suboptimal methods for signal detection
Goal: To lessen the total VLSI area of signal detector
5. Conditions and Assumptions
CONDITIONS
SAT and DAT are of duration 600ms or less
False detection of SAT and DAT signals
should be avoided (harmonics, voice, DTMF*)
Allowed frequency shift is ± 1%
Transistor count estimate
should comply to CMOS implementation constraints
ASSUMPTIONS
- Max amplitude distortion in the case of SAT is -3dB
- Max relative amplitude ratio in the case of DAT is -6dB
- Min SNR (Signal to Noise Ratio) is 10dB
- Separate detector exists for low and high frequencies
- The used VLSI logic is fast enough
to perform critical operations in real time
6. Mathematical Modeling
Signal detection based on DFT
Three samples in the frequency domain are tested,
before a decision for a particular frequency is made
Separate detectors for low and high frequencies:
The detection problem has been partitioned
The choice of DFT resolution:
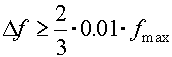
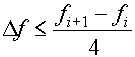 ,
,
D
f - distance between two neighboring DFT samples;
fi+1 and fi - real neighboring frequencies;
fmax - maximal frequency from the given frequency set;
7. Simulation Analysis
- Simulator of the signal detector written in C
- Different levels of quantization noise (DMF, SAS, WPD, BMF)
- Different environmental conditions:
ideal conditions, presence of Gaussian noise,
presence of pulse noise, presence of burst pulse noise
- Different types of signal distortion:
amplitude, frequency,
interference in the form of neighboring frequency from the set
- Percentage of successful detection
for every of suboptimal detection methods has been found
- Selection of the most convenient
suboptimal detection method (WPD,BMF)
- Simulation results: Percentage of successful
IEEE 1390 signal detection (low frequencies);
pulse noise case
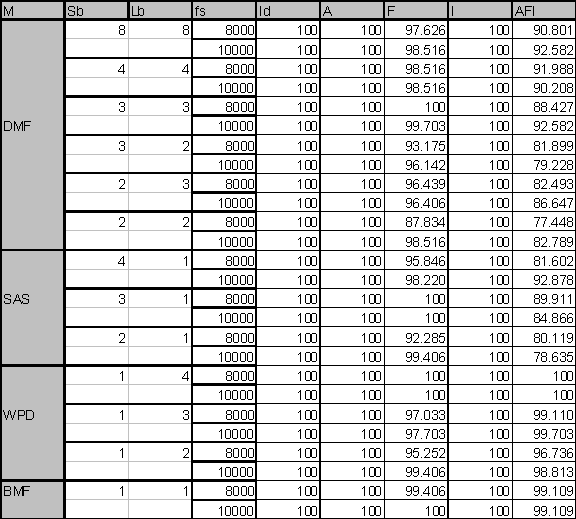
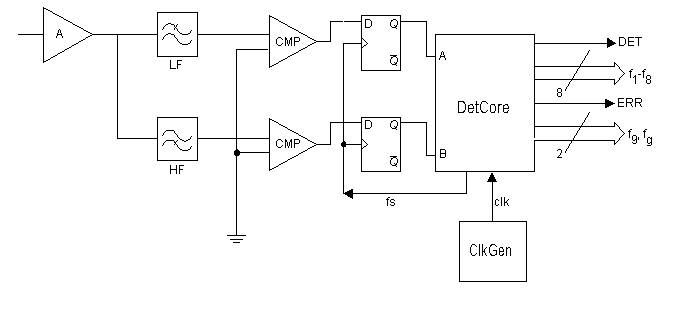
8. Implementation Analysis
Gate-level hierarchy scheme of the IEEE 1390 signal detector
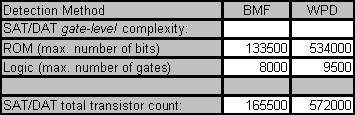
VLSI complexity estimate (max transistor count)
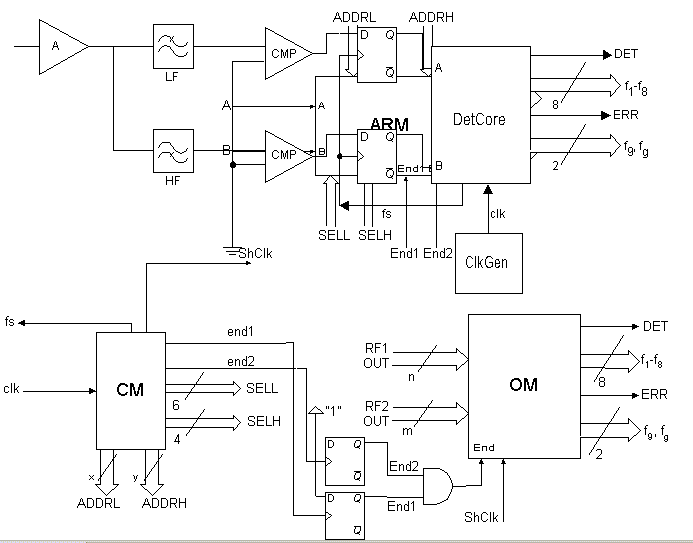
- Components of the detector core (DetCore):
CM (Control Module);
ARM (Adder, Registers, and Memory);
OM (Output Module);
9. Conclusion
Performed analyses:
Mathematical modeling
Simulation analysis
Implementation analysis
- Suggested algorithm presents a possible solution
of SAT/DAT (IEEE 1390) signal detection
- VLSI realization of the appropriate detector:
Complexity/Performance tradeoff
HDL language description of the detector
HDL model simulation and testing
VLSI implementation: silicon compilation
What is the Next Step?
Remote and virtual factories,
controlled by integrated 1390/Internet
Wireless Internet-oriented telemetry and more,
using integrated GPS/Internet
References:
[Domazet98] Domazet, D.,
"Virtual Factories on Internet,"
Technical Report, DD/1/98, Gintic Institute, Singapore
March 1998.
[Jameel98] Jameel, A., Stuempfle, M., Jiang, D., Fuchs, A.,
"Web on Wheels: Toward Internet-Enabled Cars,"
IEEE COMPUTER, January 1998, pp. 69-76.
Case Study:
Virtual Factories - Globalization in Action
Factories with no people and no light!
Different production phases at different global locations.
Example: Gintic in Singapore [Domazet98].
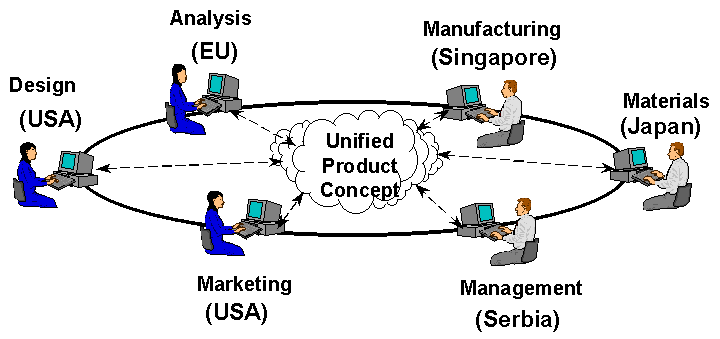
Figure 1:
The Gintic Approach
Case Study:
Web on Wheels - Telematik by Mercedes
- Internet services can be extended to customers in automobiles.
- Another issue is remote diagnostics.
- First Internet-enabled cars may hit roads before the year 2002
[Jameel98].
- Location awareness is the major prerequisite
for location sensitive services.
- Safe-to-use is the major design requirement
(no eyes off the road when email).

- Easy-to-use is another important issue
(no hands off the wheel when action).
Major services:
- Seamless access to office or home computers (e.g., email)
- Location-based information on demand (e.g., the nearest gas station)
- Remote diagnostics and roadside assistance (e.g., S.O.S.)
- Personalized services on demand (e.g., WWW access)
- Interactive audio and video for passengers (e.g., time sinks)
- Electronic commerce on Interent (e.g., smart cards)
- Electronic business on Interent (EBI)
Major issues:
- Mobile wireless communications
- System architecture
- User interface design
Mobile Wireless Communications
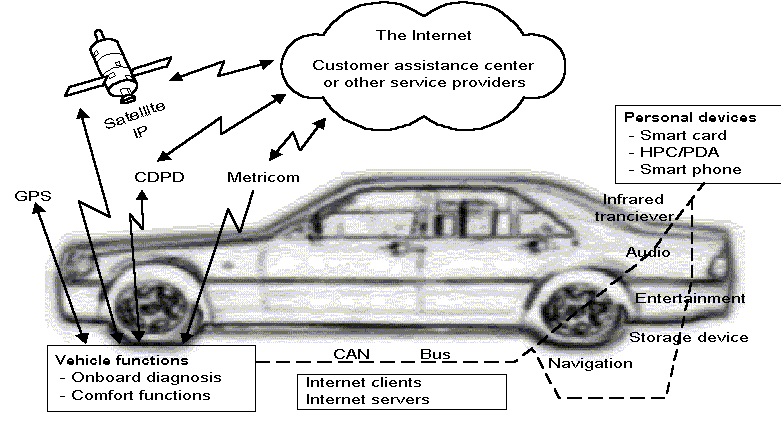
Figure 2: The Internet on Wheels Concept Car
Metricom - Metropolitan Network
(10s Kbits/s for flat montly fee)
CDPD - Cellular Digital Packet Data
HPC - High Performance Computing
PDA - Personal Digital Assistant
System Architecture
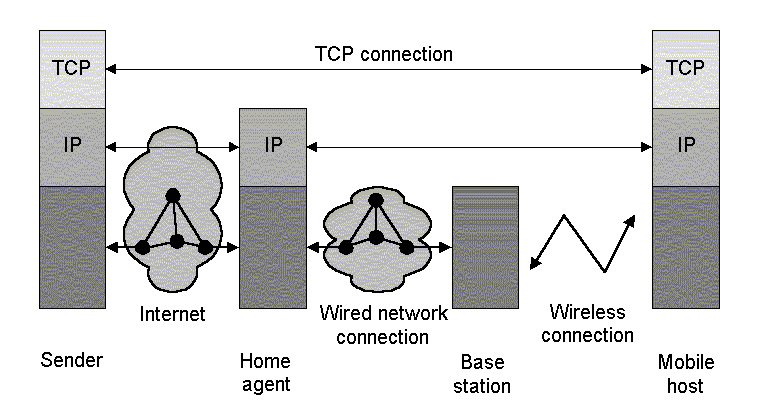
Figure 3:
The Basic Mobile IP Architecture
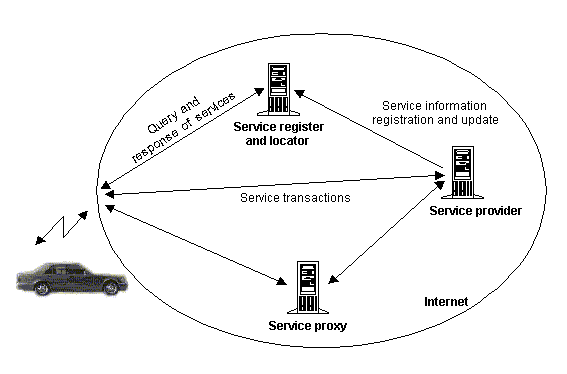
Figure 4:
The Basic Service Architecture
User Interface
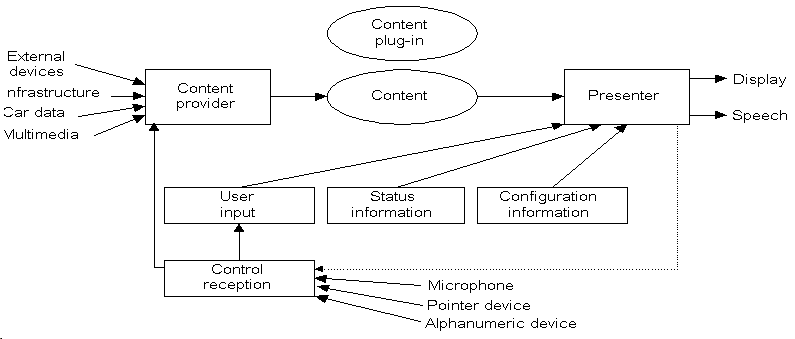
Figure 5:
The Basic User Interface Infrastructure
Major Solutions:
- One-touch
- Speech-synthesis
- Speech-recognition
Advanced Internet Services
Sinisa Cvetkovic
cvetkos@EUnet.yu
Veljko Milutinovic
vm@etf.rs

Mutations of Classical Approaches:
Internet Fax
Fax Web
Net to Phone
Net Talk
A Very Informative Reference:
[Cvetkovic98] Cvetkovic, S., "Issues in Internet for EBI",
http://galeb.etf.rs/~ebi/ or cvetkos@EUnet.yu, 1998.
Internet Fax The TCP.INT Remote Printing
Basic idea:
Sending a fax message by email to a server
which is local to the fax message destination.
Sending a real fax as a local call,
at no charge to the sender.
Checking if the destination location is covered by the service:
- Via WWW:
Visit http://www.tpc.int (option: Check Coverage)
and type in the destination fax number (starting with the country code)
- Via email:
Send email to tpccover@info.tcp.int
and specify the destination fax number.
Sending is based on several methods:
- Sending email to the address
remote-printer.USER@FAXNUMBER.iddd.tpc.int
USER includes the name and the location of the receiver '_' means 'space'
'/' means 'enter' FAXNUMBER includes no spaces, dashes, or points
(up to 15 digits).
Example
remote-printer.Veljko_Milutinovic/IFACT@381113248681.iddd.tpc.int delivers the email message to fax number +381-11-324-8681
with the following text in the header of the message:
Veljko Milutinovic IFACT
- Visiting the WWW page
http://www.tpc.int (Option: Send a Fax) and filling in a form.
- Sending a WORD or an EXCEL document
using the program HQFax which can be found at
http://www.tpc.int (Option: Client Software)
- Sending a scanned document (BMP, GIF, PCX, TIF, JPG, ...)
using the program ScanFax which can be found at
http://www.tpc.int (Option: Client Software)
Acknowledgement comes to the sender's email address
after the fax is delivered (typically after a few minutes):
time of delivery, transfer time, etc...
Internet Fax Mailbox The FaxWeb
Basic idea:
Faxes directed to a phone number get posted on WWW
Ideal for those without mobile phone/fax units

More info at http://www.faxweb.net
Internet to Phone Talk
The Net2Phone by IDT
Basic idea:
The talk is transformed into a bit stream,
and transported via Internet to a server in the USA.
At the server, it is transformed into an analog signal,
and transported via telephone network to an ordinary telephone set.
Costs are charged, based on the distance from the server in the USA.
Cost structure:
- For a PC in Yugoslavia, the savings is
from about 15 times (when the callee is in the USA),
to about 4 times (when the callee is in a neighboring European country)
- The cost has three parts:
- Local phone call (from the home to the local Internet provider).
- The Internet provider charges (about $0.01/min, in Yugoslavia).
- The IDT charges (the major part).
- The IDT charges per minute:
- London - Internet=$0.18 (YugoClassical=$0.80).
- NYC off peak - Internet=$0.10 (YugoClassical=$1.44).
- NYC peak - Internet=$0.15 (YugoClassical=$1.44).
Technical prerequisites:
- Pentium, sound card, ear set, microphone, modem (min 28800 bps).
- Prefered - provider using cable rather than satelite infrastructure.
- Software package Net2Phone (from www.net2phone.com Option:Download).
Getting started: (for details see [Cvetkovic98])
- Download and install.
- On the first login, a personal form is filled out, and a PIN is defined.
- The IDT server defines the ACCOUNT NUMBER,
used for charging purposes;
Charging:
- Up-front payment $25, $50, or $100 by credit card.
(there is a form at http://www.net2phone.com).
- Automatic charging while talking.
(there is an account balance option at http://www.net2phone.com).
- No charging for 1-800 and 1-888 numbers in the USA.
Human interface:
- Press the CALL button to initiate the call.
- Press the PUSH TO TALK button to talk (if half duplex sound card).
- Release the same button to listen (if half duplex sound card).
- Press the VOX button to activate the AUTOMATIC PUSH TO TALK.
- Press HANG UP to finish.
For more options see [Cvetkovic98].
Problems:
- Echo if satelite link used.
- Low quality if slow modem
- Classical phone set can not call a PC, for now.
Internet PC to PC Talk Net Talk
Basic idea:
 Sound is transformed into bitstream
Sound is transformed into bitstream
and transported to another PC
Camera option more popular !!!
Net Conference
Working together in an application during a meeting
NetMeeting by Microsoft (http://microsoft.com/netmeeting)
IPhone by Vocaltec (http://www.vocaltec.com)
The Mobile IP
Veljko Milutinovic
Department of Computer Engineering,
School of Electrical Engineering,
University of Belgrade
vm@etf.rs
http://galeb.etf.rs/~vm
S
Mobile Networking Terminology
Agent advertisement:
The procedure by which a mobility agent becomes known to the mobile node.
Agent discovery:
The process by which a mobile node can obtain the IP address of a home agent or foreign agent, depending upon whether the mobile node is home or away from home. Agent discovery occurs when a mobile node receives an agent advertisement, either as a result
of periodic broadcast or in response to a solicitation.
Automatic home agent discovery:
The process by which a mobile node can obtain the IP address of a home agent of its home network.
Binding:
The triplet of numbers that contains mobile node's home address, its-care-of address, and the registration lifetime - how long mobility agents can use binding.
Binding update:
The message that supplies a new binding to an entity that needs to know the new care-of address for a mobile node. The binding update contains the mobile node's home address, new care-of address, and a new registration lifetime.
Care-of address:
An IP address on the mobile node's current point of attachment to the Internet, when the mobile node is not attached to the home network. Collocated care-of address is a care-of address assigned to one of the mobile node's network interfaces, instead of
one being offered by a foreign agent.
Correspondent node:
A node that sends or receives a packet to mobile node; the correspondent node may be another mobile node or a nonmobile Internet node.
Discovery:
In this article, short for agent discovery.
Encapsulation:
The process of incorporating an original IP packet (less any preceding fields such as a MAC header) inside another IP packet, making the fields within the original IP header temporarily lose their effect.
Foreign agent:
A mobility agent on the foreign network that can assist the mobile node in receiving datagrams delivered to the care-of address.
Foreign network:
The network to which the mobile node is attached when it is not attached to its home network, and on which the care-of address is reachable from the rest of the Internet.
Fully qualified domain name (FQDN).
An Internet node's FQDN is its complete domain name as defined by the Domain Name System (DNS). A node can be known locally by a relative domain name that is a substring of its FQDN, but such a relative na
me cannot be resolved correctly by Internet nodes outside of the part of the domain name hierarchy indicated by the relative name. The fully qualified name can be resolved from anywhere in the Internet, subject to access control and routability of the res
olution request.
|
Home address:
The IP address assigned to the mobile node, making it logically appear attached to its home network.
Home agent:
A node on the home network that effectively causes the mobile node to be reachable at its home address even when the mobile node is not attached to its home network.
Home network:
The network at which the mobile node seems reachable, to the rest of the Internet, by virtue of its assigned IP address.
Minimal encapsulation:
A variant encapsulation technique specified in RFC 2003 that temporarily alters the structure of the original IP header, but uses fewer bytes for tunneling packets to the care-of address than the default method (IP-within-IP) uses.
Mobile node:
A node that, as a part of normal
use, changes its point of attachment to the Internet.
Mobility agent:
A node (typically a router) that
offers support services to mobile nodes. A mobility agent
can be either a home agent or a foreign agent.
Nomadicity:
The full range of network
technology being designed to come to the assistance of the
mobile (or nomadic) computer use, not limited to network
layer protocols.
Redirection:
A message that is intended to cause
a change in the routing behavior of the node receiving it.
Registration:
The process by which the mobile
agent informs the home agent about its current care-of
address
Remote redirection:
A redirect sent from a
source not present on the local network. The source can be
located anywhere in the global Internet and may have
malicious intent and be untraceable.
Replay attack:
A security violation whereby a
malicious entity attempts to imitate a transaction recorded
during previous and valid transaction between two
protocol entities. Both protocol entities have to be aware
that the subsequent identical traffic streams may no longer
be valid. Since the previous transaction was valid, the
algorithms for detecting replay attacks needs to
incorporate data that can never be reproduced in any
correct subsequent transaction.
Route optimization:
A process that enables the
delivery of packets directly to the care-of address from a
correspondent node without having to detour through the
home network.
Source routing:
A routing technique that causes
some or all intermediate routing points to be represented
directly in the data packet to be forwarded This is in
contrast to the typical situation in which intermediate
routers rely on acquired routing state information to
forward incoming packets.
Tunneling:
The same as encapsulation, but with
additional connotations about changing the effects of
Internet routing on the original IP packets.
|
The Mobile IP (RFC 2002)
Essence:
Increasing variety of wireless devices offering IP connectivity
(PDAs, handhelds, and digital cellular phones).
Making mobility transparent to applications
and higher level protocols (TCP, ...).
Using two IP addresses: a fixed home address
plus a care-of address that changes at each new point of attachment.
Major mechanisms:
- Discovering the care-of address
- Registering the care-of address
- Tunneling the care-of address
Introduction into mobile IP
The IP routes packets from a source to a destination
by allowing routers to forward packets according to routing tables
(destination network number obtained by masking some of the lower IP bits).
Mobile IP requires the existence of a network node known as home agent.
Also, at the new point of attachment, a foreign agent is involved.
Whenever mobile node away from its home network (at a foreign network),
home agent gets all the packages and forwards them
to the mobile node's current point of attachment
(through an interaction with the foreign agent).
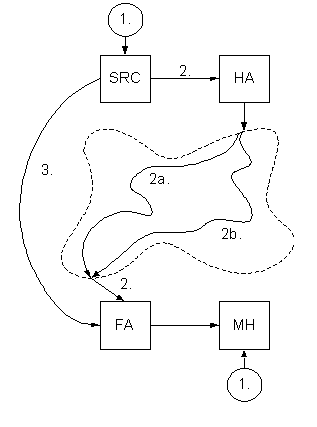
The discovery process
Whenever the mobile node moves,
it obtains its new care-of address through the discovery process,
based on the router advertising protocol (extension of the RFC 1256).
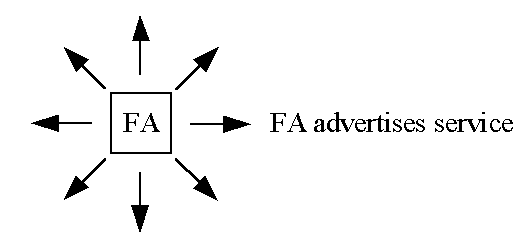
Discovery operations in mobile IP (FA is foreign agent). FA advertises:
- about care-of addresses,
- about special services, and
- about the visiting mobile agents (push versus pull)
The registering process
Next, the new care-of address is registered with its home agent,
so the first next packet can be forwarded.
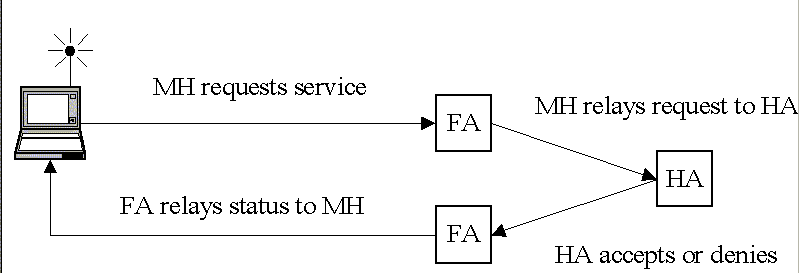
MH - Mobile Host
HA - Home Agent
FA - Foreign Agent
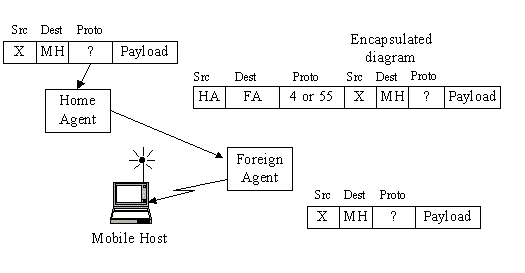
The tunneling process
Further delivery requires that the care-of address appears as destination IP.
This transformation is called redirection.
Home agent redirects packets from the home network to the care-of address,
by constructing a new IP header.
The new header encapsulates the original packet
causing the mobile's node home address to have no effect on packet routing.
The inverse transformation is done by the foreign agent.
Such encapsulation is called tunneling.
The ongoing research
Security improvement (making it more secure)
Route optimization (bypassing the home)
Source routing
(moving different outgoing and reply routers)
The mobile IP WWW resources
Mobile IP working group drafts and documents
http://www.ietf.org/html.charters/mobileip-charter.html
Stanford MosquitoNet Mobile IP project
http://mosquitonet.stanford.edu/software/mip.html
The CMU Monarch project
http://www.monarch.cs.cmu.edu/
Portland State Secure Mobile Networking project
http://www.cs.pdx.edu/research/SMN/
State University of New York at Binghamton Linux-Mobile IP project
http://anchor.cs.binghamtom.edu/~mobileip/
Research at UB/IFACT
Suboptimal detection and correlation Issues:
Optimal versus suboptimal
Problems reincarnate-experiences accumulate
On-hook: Suboptimal detection
Off-hook: Suboptimal correlation
Acknowledgments: Goran Davidovic and Miljan Vuletic Papers: M+M (2)



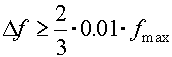
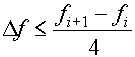 ,
,